What is an SPN, How Does Kerberos Work, and Why Are Duplicate SPNs a Problem?
What is an SPN in an Active Directory Environment?
An SPN is an attribute defined according to a specific format that uniquely identifies a service. Within the same domain in Active Directory, each SPN must be configured to be unique. SPNs are used for managing popular applications such as MSSQL, IIS, EXCHANGE, and SAP, as well as for creating and verifying Service Tickets within the Kerberos protocol. SPNs can typically be obtained by computer objects, service accounts (gmsas), or users. However, it's important to note that these accounts are often granted excessive privileges. For example, these accounts are frequently included in authorized groups (such as Administrators or Domain Admins), increasing security risks.
Why Is SPN Important?
In Active Directory (AD) environments, Service Principal Name (SPN) records play a critical role in service authentication processes. SPNs are unique identifiers that ensure clients access the correct service and are used by the Kerberos protocol for authentication. However, when SPNs are configured incorrectly or conflict with each other, serious problems can occur in authentication systems. So, what exactly is an SPN, and how are they used?
SPN and Kerberos Protocol
Kerberos is a secure authentication protocol used in large, distributed systems. Developed by MIT, Kerberos operates through a centralized Authentication Server (KDC). The KDC has two main components:
- Authentication Server (AS): Performs user authentication.
- Ticket Granting Server (TGS): Gives the user a "ticket" for the service he/she wants to access.
Featured Features
- Secure Encryption: All communication is encrypted and strong encryption algorithms are used.
- Ticket Based System: Once verified, the user does not need to authenticate again.
- Mutual Authentication: Both client and server authenticate each other.
Advantages
- Prevents password transmission over the network.
- It offers a scalable solution in distributed systems.
Disadvantages
- Time Synchronization: The clocks of servers and clients must be synchronized.
- Critical Role: KDC downtime blocks the entire authentication process.
Authentication Process with Kerberos Ticket
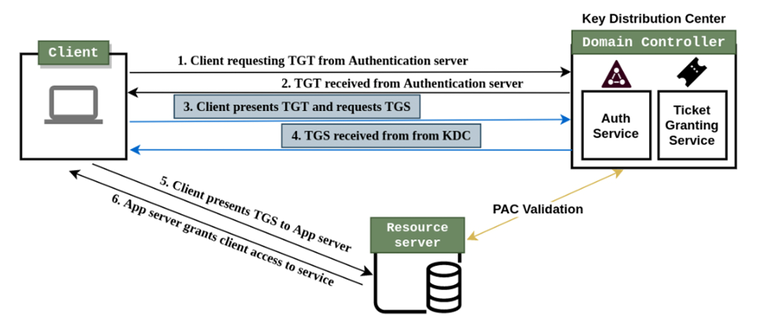
The Kerberos authentication process occurs in the following steps:
- The client requests an authentication ticket (TGT) from the KDC.
- The KDC verifies and sends a session key along with the encrypted TGT.
- The client stores the TGT and requests a new TGT if it expires.
- The client passes TGT to TGS to access a service.
- TGS checks the user's authorization to access the service and sends a session key.
- The client authenticates itself by passing this session key to the service and access is granted.
What is a Duplicate SPN and How Does It Form?
SPNs are stored as attributes of objects in the Active Directory database and must be unique. Defining the same SPN across multiple accounts (duplicate SPNs) can lead to authentication issues. Therefore, identifying and resolving duplicate SPNs is crucial.
The main reasons for this situation are:
- Assigning the same SPN to more than one account or computer object when creating service accounts or servers.
- Moving a service to a new server but not removing the SPN on the old server.
- Re-defining the same SPN when copying or backing up services.
- Inadvertently manually assigning SPNs to multiple accounts or servers.
Damages of Duplicate SPN Records
Duplicate SPNs can cause various problems in an Active Directory environment. They can negatively impact system security and performance, particularly by affecting Kerberos authentication processes.
The Kerberos protocol expects each SPN to be defined for only one account. However, with duplicate SPNs, clients have difficulty finding the correct server, which can lead to login errors and service interruptions.
Duplicate SPNs can cause clients to be redirected to the wrong servers. This creates vulnerabilities that can lead to credential theft. The system can become particularly vulnerable to man-in-the-middle (MITM) attacks.
Duplicate SPNs can cause problems accessing services that require authentication, such as databases or web servers. As a result, performance can be degraded or the service can become completely unavailable.
Duplicate SPN errors frequently result in authentication failures and conflict records in Active Directory and Kerberos logs.
Where is SPN used?
SPNs play a critical role in many different scenarios.
IIS (Internet Information Services)
IIS servers use SPNs to securely authenticate web applications based on Kerberos. Proper configuration of SPNs is crucial, especially in intranet environments.
Microsoft SQL Server
In SQL Server, SPN records are used to authenticate database connections. When SPNs are configured incorrectly, Kerberos authentication can fail and less secure protocols (such as NTLM) can be used.
Exchange Server
Services on Exchange Server (for example, Outlook Web App or EWS) use SPNs for secure authentication of users.
Azure Active Directory
In hybrid authentication scenarios, SPNs enable Kerberos to work seamlessly between Azure AD and on-premises systems.
SharePoint
SPNs support secure authentication of users' credentials across SharePoint services and enable the Kerberos-based authorization mechanism.
Managing and Configuring SPNs
SPNs are managed using the setspn tool in the Active Directory environment.
Adding a New SPN Record
setspn -A MSSQLSvc/servername.domainname.com:1433 domain\servicename
Duplicate SPN Control
setspn -X
Deleting a SPN
setspn -x service_account /servername.domainname.com
Listing Available SPNs
setspn -L domain\service_account
Listing All SPNs (PowerShell):
Get-ADObject -Filter {servicePrincipalName -like "*"} -Properties servicePrincipalName | Select-Object Name, servicePrincipalName
In an Active Directory environment, SPNs play a vital role in secure and efficient authentication processes. However, incorrectly configured SPNs can lead to security vulnerabilities and operational issues. Therefore, proper SPN management, including the detection and removal of duplicate records, should be performed regularly.
By configuring your SPNs correctly, you can optimize the security and operation of your Active Directory environment.
